Maritime Cyber Security Practices
In recent months, we witnessed a tragedy in Ukraine. In military operations, we noticed the capabilities of hackers. They could damage power grids, supply chains, banking systems, water treatment, and communications. Targets of maritime interest were transportation infrastructures and ports. As per a report by Microsoft, the success of such cyber-attacks is achievable through social engineering. This practice allows targeting careless or untrained employees. In addition, several studies on cyber-attacks highlighted real ship navigation risks. Some with navigation interests are:
- AIS Denial-of-Service (DoS), spoofing
- Message flooding
- GPS spoofing
- RADAR antenna exploitation
- ECDIS image freezing
You can find details of the latest papers and examples of such attacks below.
Cyberwarfare Examples
Some published notable cases are the below:
• In February 2022, intelligence information on the Ukrainian military offices and government networks leaked.
• On January 15, 2022, a ransomware attack, targeted the government, non-profit organizations and IT institutions based in Ukraine
• On January 24, 2022, a cyber-attack that disrupted the operations of the railway system in Belarus slowed down the movement of Russian forces.
• On June 19, 2021, an online ship-tracking site showed that a British warship and a Dutch frigate were close to Sevastopol in Crimea, which escalated tension between Russia and Britain. Both ships were roughly 300 km away.
However, similar military operations have been worldwide such as:
• In Operation Orchard, the Israeli air force attacked a Syrian radar system without being noticed. It is believed that an Electromagnetic Attack triggered preinstalled malicious software on the Syrian radar.
• The famous case of the Stuxnet malware attack at an Iranian Facility in 2010 showed that sophisticated attacks might require the cooperation of highly qualified human resources from different technical fields. However, a hacker's cooperation with a marine professional should not be seen as a distant scenario. Moreover, the Stuxnet case revealed a USB stick's damage even to an isolated facility.
• In 2015, a cyber-attack caused a blackout for several hours in western Ukraine and part of Kyiv.
Maritime Cyber Security Regulations
The International Maritime Organization (IMO) presented the MSC.428 (98) as a reaction to cyber-crime. Its enforcement date was in 2021. To comply with the ship, managers should revise their strategies to address ship and company cyber-attacks. This means ships' security plans and safety management systems need revisions (MSC.1/Circ.1526). The IMO is likewise working with the International Electrotechnical Commission (IEC) the IEC 63154 "Online protection General Requirements, Methods of Testing and Required Test Results."
What is the Current Status in the Maritime Industry?
A 2021 paper revealed several technical and training cyber issues in merchant ships. Since then, several studies have shown vulnerabilities in ship navigation systems. As a result, it is clear that the ship's networks and data are targets today.
Top ship threats are Malware Injection in a target system (i.e., a radar computer or an ECDIS computer connected to an AIS receiver). This can occur by exploiting removable media vulnerabilities or even supply chain attacks. Let us consider navy cases to get an idea of preinstalled malware threats. The USA Navy warships and CIA drone operations were reportedly implanted with microchips to enable hacking. In addition, it is believed that Trojan horses have already compromised the US Navy's systems. This happened due to the service's legacy use of "open" commercial systems.
Maritime Cyber Security Incidents
Current military operations allow us to think about cyber threats on ships. Modern ships have similar technologies, including ECDIS, AIS, ERP Software and VOIP communications. These devices, combined with weak procedures and lack of awareness, generate multiple cyber threats on ships.
AIS Denial-of-Service (DoS), Spoofing
Recent research by Khandker et al. (2022) has shown that AIS can be compromised. The AIS protocol does not utilise authentication or encryption via remote radio frequency (RF) links using transmission-enabled software-defined radio (SDR). A cyber-electronic attack on ships could be succeeded with an offence Electronic Warfare (EW) method through the electromagnetic spectrum. In the market exist transmission-enabled SDR products such as HackRF and BladeRF for less than $500. It is proven that these devices can produce fake AIS signals. Approximately 89% of the setups can be affected by Denial-of-Service (DoS) attacks at the AIS protocol level. Other attack ideas may include spoofing and message flooding. Furthermore, malicious commands can be transmitted to the ECDIS when connected with AIS.
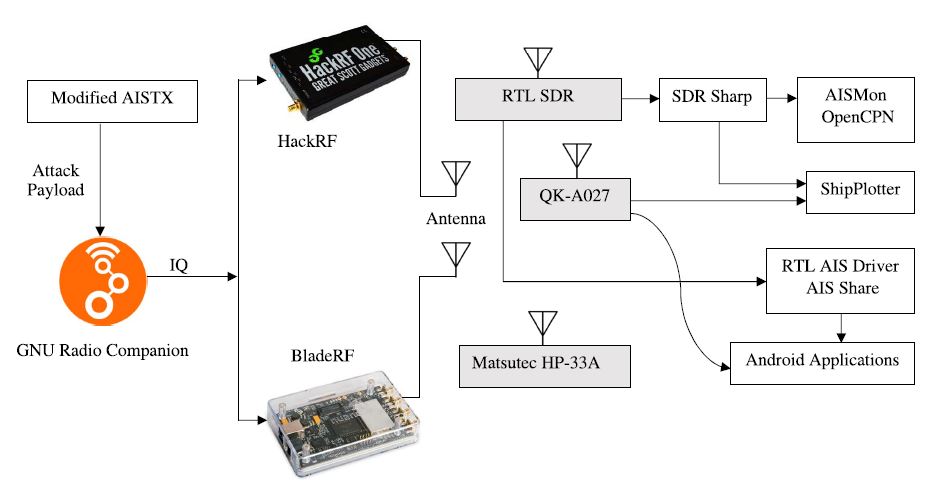
(Source Khandker et al 2022)
RADAR Antenna Exploitation
Operation Orchard initiated the discussion of cybersecurity of naval systems. Research for marine radars has shown that a radar antenna can be exploited as an open door for receiving malicious commands remotely. As a result, target detection information is manipulated, but the radar computational process continues to run normally (Leite Junior et al., 2020, Leite Junior et al., 2021)
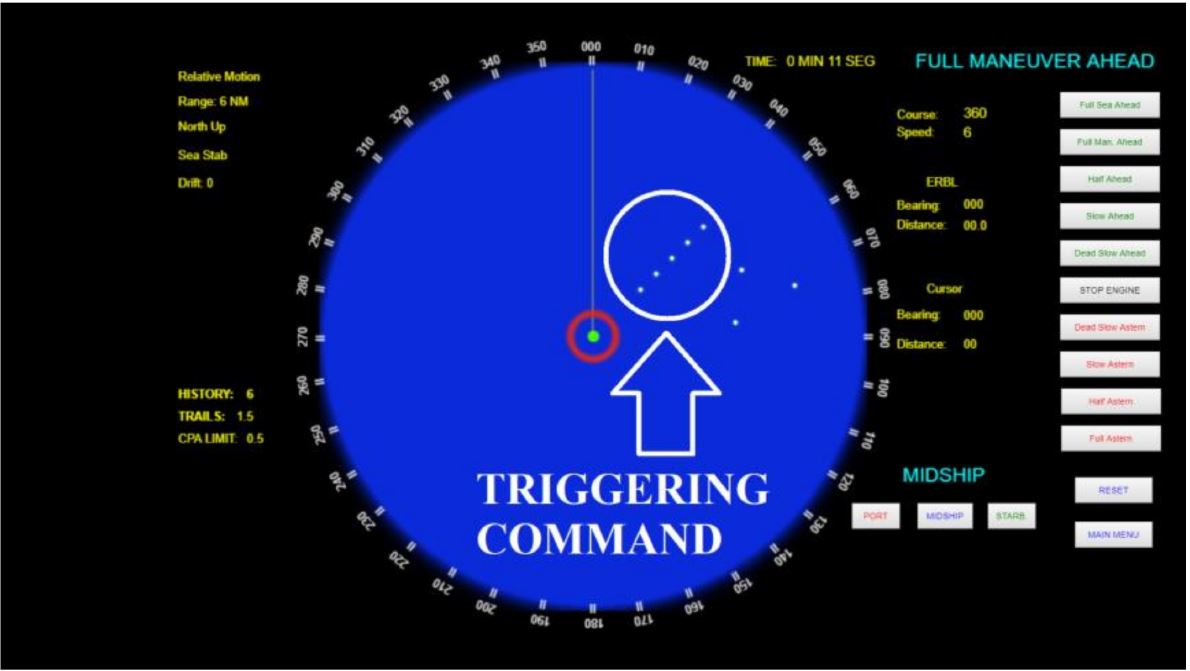
(Source Leite et al 2020)
GPS Spoofing
GPS spoofing attacks are a well-known threat to ships' safe navigation. Attacks on GPS signals can affect the time synchronisation of individual devices. Cases have been reported in East Mediterranean and other territories.
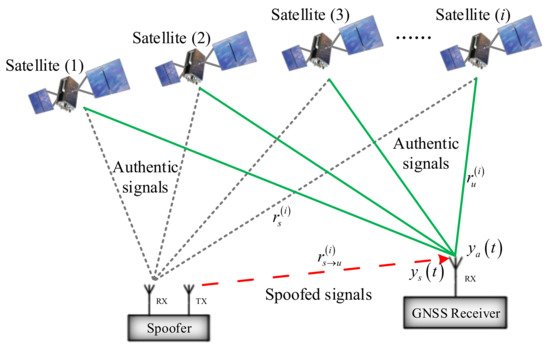 GPS Spoofing
GPS Spoofing
(Source: Liu et al 2018)
ECDIS Image Freezing
The safe operation of Electronic Navigation Charts (ECDIS) is based on a regular update of electronic charts. Thi process is achieved either online or with a mass storage device such as USB, CD/DVD. In case of infection, e-navigation chart images may freeze, sensitive data may be lost, or remote EDCIS control is established. In addition, an infected LAN could affect when ECDIS is connected to the ship’s internet.
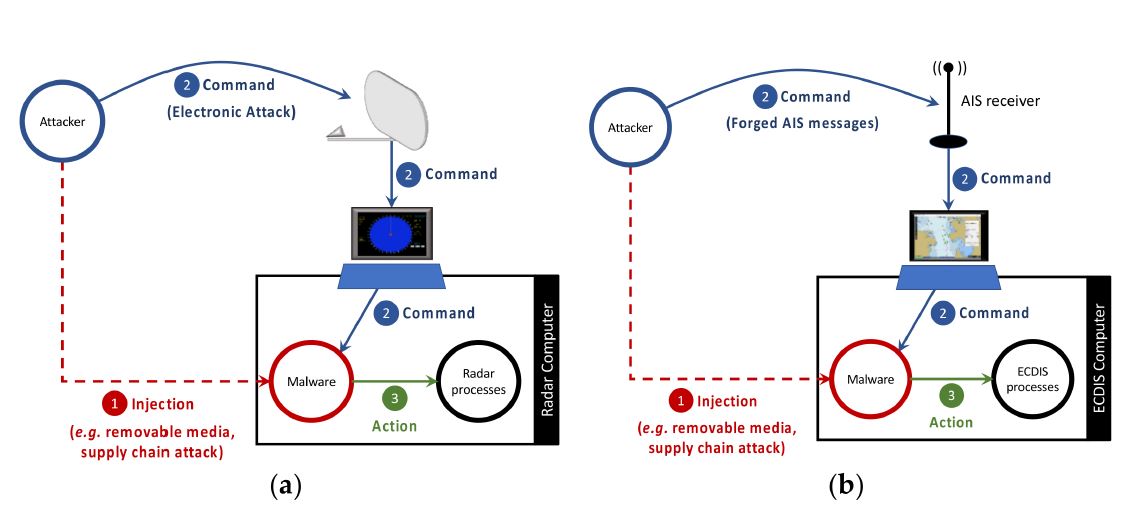
(Source Leite et al 2021)
Maritime Cyber Security Solutions
Interviews and audits on 15 ships with 315 seafarers showed huge security holes because of training absence. Still, physical security and network protection that, as of now, apply to ships are critical security qualities.
A reasonable question is how cyber-attacks are so successful even in military systems. The answer is through social engineering. This widespread practice targets careless or untrained employees. Microsoft released a report revealing that most of these attacks were associated with the below:
• Exploitation of public facing applications or spear-phishing with attachments/links for initial access.
• Credential theft and use of valid accounts throughout the attack lifecycle, making “identities” a key intrusion vector. This includes within Active Directory Domain and through VPNs or other remote access solutions.
Further risks emerge from seafarers' devices using the ship's WI-FI, Bluetooth or SIM cards provided by unknown vendors. Examples are laptops, Tablets, Smartphones, Smartwatches and other IoT Devices.
Training
Cyber security awareness should be part of scheduled training sessions. A ship's crew should know relevant procedures in each company's SMS & SSP manuals. Keep in mind that most attacks are initiated by malware. These programs are downloaded through social engineering and spread on the ship's network with USB devices. A designated officer should conduct the ship's Cyber hygiene.
Practical Navigation
As part of the emergency navigation planning, deck officers should be aware of developing and following a passage plan that includes cyber-attacks. Additionally, a position fix should always be carried out with secondary means (RADAR, Bearings etc.), especially near coasts.
Bibliography
• BBC News. “Hackers Caused Power Cut in Western Ukraine - US.” BBC.com, 12 Jan. 2016, www.bbc.com/news/technology-35297464. Accessed 20 Feb. 2022.
• Gard P&I Club 2020, GPS interference and jamming on the increase. https://www.gard.no/web/updates/content/30454065/gps-interference-and-jamming-on-the-increase
• Grigoriadis, C., Laborde, R., Verdier, A., & Kotzanikolaou, P. (2021). An Adaptive, Situation-Based Risk Assessment and Security Enforcement Framework for the Maritime Sector. Sensors, 22(1), 238.
• Karahalios, H. Appraisal of a Ship’s Cybersecurity efficiency: the case of piracy. J Transp Secur 13, 179–201 (2020). https://doi.org/10.1007/s12198-020-00223-1
• Khandker, S., Turtiainen, H., Costin, A., & Hämäläinen, T. (2022). Cybersecurity Attacks on Software Logic and Error Handling Within AIS Implementations: A Systematic Testing of Resilience. IEEE Access, 10, 29493-29505.
• Leite Junior, W. C., & de Sá, A. O. Triggering Cyber-electronic Attacks in Naval Radar Systems. 2020 IMEKO TC-19 International Workshop on Metrology for the Sea Naples, Italy, October 5-7, 2020
• Leite Junior, W. C., de Moraes, C. C., de Albuquerque, C. E., Machado, R. C. S., & de Sá, A. O. (2021). A triggering mechanism for cyber-attacks in naval sensors and systems. Sensors, 21(9), 3195.
• Liu, Y., Li, S., Fu, Q., & Liu, Z. (2018). Impact assessment of GNSS spoofing attacks on INS/GNSS integrated navigation system. Sensors, 18(5), 1433.
• Microsoft Security Blog. “ACTINIUM Targets Ukrainian Organizations.” Microsoft.com, 4 Feb. 2022, www.microsoft.com/security/blog/2022/02/04/actinium-targets-ukrainian-organizations/. Accessed 20 Feb. 2022.
• Microsoft Security Blog. “Destructive Malware Targeting Ukrainian Organizations.” Microsoft.com, 16 Jan. 2022, www.microsoft.com/security/blog/2022/01/15/destructive-malware-targeting-ukrainian-organizations/. Accessed 20 Feb. 2022.
• Microsoft Special Report: Ukraine An overview of Russia’s cyberattack activity in Ukraine https://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE4Vwwd
• Pietsch, Bryan. “Hacking Group Claims Control of Belarusian Railroads in Move to ‘Disrupt’ Russian Troops Heading near Ukraine.” Washington Post, 25 Jan. 2022, www.washingtonpost.com/world/2022/01/25/belarus-railway-hacktivist-russia-ukraine-cyberattack/.
• Sestak, J. (2021). The US Navy’s Loss of Command of the Seas to China and How to Regain It (Winter 2021). Texas National Security Review.
• Stuart Madnick What Russia’s Ongoing Cyberattacks in Ukraine Suggest About the Future of Cyber Warfare https://hbr.org/2022/03/what-russias-ongoing-cyberattacks-in-ukraine-suggest-about-the-future-of-cyber-warfare
• Sviličić, B., Rudan, I., Francic, V., & Doričić, M. (2019). Shipboard ECDIS Cyber Security. Pomorstvo, 33, 176-180.
• ENISA (2019) Port Cybersecurity - good practices for cybersecurity in the maritime sector ISBN 978-92-9204-314-8, DOI: https://doi.org/10.2824/328515
• Boyes H (2015) Cybersecurity and cyber-resilient supply chains. Technol Innov Manage Rev 5(4):28–34
• Khandker, S., Turtiainen, H., Costin, A., & Hämäläinen, T. (2022). Cybersecurity Attacks on Software Logic and Error Handling Within AIS Implementations: A Systematic Testing of Resilience. IEEE Access, 10, 29493-29505.
• W. C. Leite Junior, C. C. de Moraes, C. E. P. de Albuquerque, R. C. S. Machado, and A. O. de Sá, ``A triggering mechanism for cyberattacks in naval sensors and systems,'' Sensors, vol. 21, no. 9, p. 3195, May 2021.
• W. C. Leite Junior, and A. O. de Sá, Triggering Cyber-electronic Attacks in Naval Radar Systems 2020 IMEKO TC-19 International Workshop on Metrology for the Sea Naples, Italy, October 5-7, 2020

